Inside Job? Millions Stolen Through Office365 Executive Email Compromise
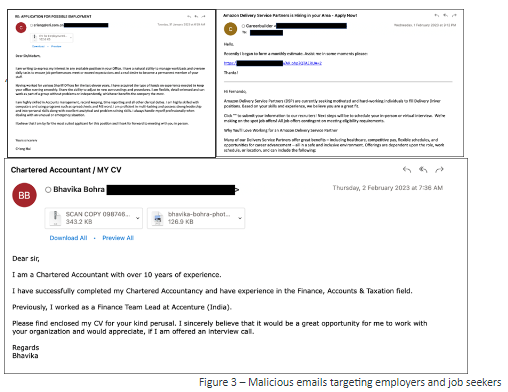
Table of Contents
Understanding Office365 Executive Email Compromise (EEC)
How EEC Attacks Work
Office365 executive email compromise attacks are highly sophisticated, often leveraging a combination of phishing, social engineering, and malware. Attackers meticulously craft deceptive emails that appear to originate from trusted sources, such as a CEO, board member, or trusted vendor. These spear phishing emails often contain malicious links or attachments designed to deliver malware or gain access to the victim's account.
- Spear Phishing Emails: These emails are highly targeted, mimicking the communication style and subject matter of legitimate emails from known individuals.
- Compromised Accounts: Attackers may gain access to legitimate accounts through password breaches, exploiting weak passwords or using credential stuffing techniques.
- Malicious Links/Attachments: Clicking on malicious links can redirect victims to phishing websites designed to steal credentials, while malicious attachments can install malware that provides persistent access to the system.
- Multi-Factor Authentication (MFA) Bypass: Sophisticated attackers are increasingly finding ways to bypass MFA, either through social engineering or by exploiting vulnerabilities in the MFA system itself.
The Human Element in EEC Attacks
The success of many EEC attacks hinges on exploiting human vulnerabilities. Attackers leverage psychology to manipulate victims into taking actions they wouldn't normally take.
- Urgency: Creating a sense of urgency, such as an impending deadline or a critical financial transaction, pressures victims into making hasty decisions without proper verification.
- Trust: Attackers exploit the trust placed in senior executives or trusted business partners to legitimize fraudulent requests.
- Lack of Awareness: Insufficient security awareness training leaves employees susceptible to phishing scams and social engineering tactics.
Investing in comprehensive security awareness training is paramount to mitigating the risk of falling victim to these attacks. Employees need to be educated on identifying suspicious emails, verifying requests from executives, and understanding the importance of strong password hygiene.
The Financial Ramifications of EEC Attacks
The Cost of Data Breaches and Financial Losses
The financial impact of successful EEC attacks can be catastrophic. Direct financial losses, resulting from wire transfer fraud, account takeover, and intellectual property theft, are only the tip of the iceberg.
- Wire Transfer Fraud: Attackers often instruct victims to transfer large sums of money to fraudulent accounts.
- Account Takeover: Compromised accounts can be used to make unauthorized purchases, access sensitive data, and disrupt business operations.
- Intellectual Property Theft: Confidential business information, trade secrets, and intellectual property can be stolen and sold to competitors.
- Reputational Damage: Data breaches and financial losses damage a company's reputation, leading to loss of customer trust and business opportunities.
The FBI's Internet Crime Complaint Center (IC3) reports millions of dollars lost annually to BEC scams, with individual incidents often costing businesses hundreds of thousands or even millions of dollars.
Insurance and Recovery Costs
Recovering stolen funds after an EEC attack is incredibly difficult, often requiring extensive legal action and forensic investigations. Cyber insurance policies can help mitigate some of the financial impact, but they are increasingly expensive and may not cover all losses.
- Insurance Claim Challenges: Proving the legitimacy of the claim and providing sufficient evidence can be challenging and time-consuming.
- Coverage Limitations: Many policies have specific exclusions and limitations, leaving businesses vulnerable to significant uncovered losses.
Protecting Your Organization from Office365 Executive Email Compromise
Implementing Robust Security Measures
Proactive security measures are crucial in preventing Office365 executive email compromise. Implementing a multi-layered approach that combines technological solutions with robust security policies is essential.
- Multi-Factor Authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of authentication to access accounts.
- Email Security Solutions: Advanced email security solutions can detect and filter malicious emails before they reach employees' inboxes.
- Advanced Threat Protection (ATP): ATP solutions provide advanced threat detection and response capabilities, identifying and neutralizing sophisticated attacks.
- Strong Password Policies: Enforce strong password policies and implement password management tools.
- Regular Security Audits: Conduct regular security audits to identify vulnerabilities and ensure security controls are effective.
The Importance of Employee Training and Awareness
No technological solution is foolproof. Employee training is a critical component of a comprehensive security strategy. Regular, engaging security awareness training programs are crucial.
- Phishing Simulations: Conduct regular phishing simulations to test employees' susceptibility and reinforce training.
- Social Engineering Awareness: Educate employees on common social engineering tactics and how to identify and respond to suspicious communications.
- Best Practices: Provide clear guidelines on best practices for email security, password management, and handling sensitive information.
Conclusion
Office365 executive email compromise represents a significant threat to businesses of all sizes, resulting in substantial financial losses and reputational damage. By understanding the mechanics of these attacks, investing in robust security measures, and providing comprehensive employee training, organizations can significantly reduce their risk. Don't become another statistic. Invest in robust security measures and employee training to safeguard your organization from the devastating effects of Office365 executive email compromise. For further information on protecting your business from BEC and EEC attacks, consult resources from the FBI's IC3 and leading cybersecurity firms.

Featured Posts
-
 Southeast Asia Energy Market Opportunities For Canadian Businesses
Apr 28, 2025
Southeast Asia Energy Market Opportunities For Canadian Businesses
Apr 28, 2025 -
 Alberta Faces Economic Fallout From Dow Project Delay Due To Tariffs
Apr 28, 2025
Alberta Faces Economic Fallout From Dow Project Delay Due To Tariffs
Apr 28, 2025 -
 Analysis The Mets Starting Pitchers Competitive Edge
Apr 28, 2025
Analysis The Mets Starting Pitchers Competitive Edge
Apr 28, 2025 -
 Ev Mandate Opposition Grows Car Dealers Push Back
Apr 28, 2025
Ev Mandate Opposition Grows Car Dealers Push Back
Apr 28, 2025 -
 Richard Jefferson Takes A Jab At Shaq The Story Behind The Comment
Apr 28, 2025
Richard Jefferson Takes A Jab At Shaq The Story Behind The Comment
Apr 28, 2025
