Crook Made Millions By Hacking Executive Office365 Inboxes: FBI Investigation

Table of Contents
The Modus Operandi: How the Hacker Targeted Executive Office365 Accounts
The hacker employed a multi-pronged approach, leveraging several techniques to breach the seemingly impenetrable security of executive Office365 accounts. This wasn't a simple phishing attempt; it was a carefully orchestrated campaign demonstrating a high level of technical skill and knowledge of their targets.
-
Spear Phishing Mastery: The attacker likely utilized highly targeted spear phishing emails. These emails were meticulously crafted to mimic legitimate communications from trusted sources, such as colleagues, clients, or even the victim's own organization. The emails often contained urgent requests, enticing links, or attachments designed to lure unsuspecting executives into revealing their credentials or downloading malicious software.
-
Malware Deployment: Once initial access was gained, sophisticated malware was likely deployed to maintain persistent access to the compromised accounts. This malware could range from keyloggers recording keystrokes to more advanced tools capable of bypassing multi-factor authentication (MFA) and exfiltrating data undetected.
-
Multi-Factor Authentication Bypass (MFA Bypass): While MFA is a crucial security layer, the attacker likely employed techniques to bypass it. This could involve exploiting vulnerabilities in the MFA system itself, using social engineering tactics to obtain one-time codes, or deploying malware designed to intercept authentication requests.
-
Data Exfiltration: After gaining access, the hacker systematically exfiltrated sensitive financial information and internal communications. This data was crucial for executing wire fraud and other financial schemes. The access likely included email threads, financial documents, and internal memos containing crucial details for the fraudulent activities.
The Financial Ramifications: Millions Lost Through Wire Fraud and Other Schemes
The financial consequences of this Office365 hacking operation are staggering. The estimated amount of money stolen is in the millions of dollars, causing significant financial losses for the targeted businesses and individuals.
-
Wire Fraud and BEC: The stolen information was used to orchestrate wire fraud schemes and other forms of Business Email Compromise (BEC). The hacker convincingly impersonated executives, instructing financial departments to transfer large sums of money to fraudulent accounts.
-
Account Takeover: Beyond wire fraud, the hacker likely used the compromised accounts to initiate other fraudulent transactions, potentially including unauthorized purchases, contract alterations, or even identity theft.
-
Reputational Damage: The financial losses were compounded by reputational damage to the victim organizations. The breach eroded trust among stakeholders, potentially leading to further financial losses and a decline in business relationships.
-
Legal Repercussions: Victims of this sophisticated fraud are likely facing considerable legal and financial challenges, requiring extensive investigation and potentially leading to costly litigation.
The FBI Investigation: Tracking the Crook and Uncovering the Network
The FBI's investigation into this complex Office365 hacking scheme is ongoing, utilizing advanced digital forensics techniques to track the perpetrator and uncover any potential accomplices.
-
Digital Forensics: Investigators are meticulously analyzing digital evidence to reconstruct the attacker's actions, identify the malware used, and trace the flow of funds. This includes analyzing network logs, email headers, and transaction records.
-
Arrests and Indictments: While specifics remain confidential during the ongoing investigation, any arrests made or indictments issued will likely be made public in due course.
-
Criminal Network: The investigation may reveal the involvement of a larger criminal network responsible for coordinating and executing these types of attacks.
-
Asset Recovery: The FBI is actively working to recover any stolen assets or funds, a process that can be protracted and complex, particularly in cases involving international transfers and cryptocurrency.
Protecting Your Office365 Account: Best Practices for Enhanced Security
The Office365 hacking case underscores the critical need for robust security measures to protect against sophisticated cyberattacks. Implementing these best practices can significantly reduce your organization's vulnerability.
-
Strong Passwords and MFA: The cornerstone of any strong security posture is strong, unique passwords for each account, coupled with the mandatory use of multi-factor authentication (MFA). MFA adds an extra layer of security, making it significantly harder for attackers to gain access even if they obtain your password.
-
Security Awareness Training: Regular cybersecurity awareness training for all employees is crucial. Training should focus on identifying and avoiding phishing scams, recognizing malicious links and attachments, and understanding the importance of reporting suspicious activity.
-
Data Loss Prevention (DLP): Implementing DLP measures helps prevent sensitive data from leaving your organization's network without authorization. This can include policies limiting the sharing of sensitive files, monitoring email traffic for suspicious activity, and using encryption to protect data at rest and in transit.
-
Regular Security Audits and Updates: Regular security audits of your Office365 environment are essential to identify and address vulnerabilities. Keeping your systems and software up-to-date with the latest security patches is also crucial to mitigate known risks.
-
Advanced Threat Protection: Consider utilizing Microsoft's advanced threat protection features, which can offer enhanced protection against sophisticated phishing attacks and malware.
Conclusion
The FBI's investigation into this millions-dollar Office365 hacking scheme highlights the ever-growing threat of sophisticated cybercrime targeting businesses and high-profile individuals. The attacker's methods demonstrate the urgent need for robust security measures, including strong passwords, multi-factor authentication, and comprehensive employee training. The significant financial losses underscore the critical importance of proactive cybersecurity strategies, and the need for constant vigilance against evolving threat vectors.
Call to Action: Don't become the next victim of an Office365 hacking attack. Strengthen your organization's cybersecurity posture today by implementing advanced security protocols and educating your employees about email security threats. Learn more about protecting your Office365 environment and preventing costly data breaches. Invest in robust Office365 security solutions and prioritize cybersecurity training to safeguard your valuable data and financial assets.

Featured Posts
-
 Chainalysis Acquisition Of Alterya Expanding Ai Capabilities In Blockchain
Apr 24, 2025
Chainalysis Acquisition Of Alterya Expanding Ai Capabilities In Blockchain
Apr 24, 2025 -
 Pope Francis Legacy A More Global Yet Divided Church
Apr 24, 2025
Pope Francis Legacy A More Global Yet Divided Church
Apr 24, 2025 -
 John Travolta Speaks Out After Private Bedroom Photo Surfaces Online
Apr 24, 2025
John Travolta Speaks Out After Private Bedroom Photo Surfaces Online
Apr 24, 2025 -
 Tina Knowles Breast Cancer Diagnosis The Importance Of Mammograms
Apr 24, 2025
Tina Knowles Breast Cancer Diagnosis The Importance Of Mammograms
Apr 24, 2025 -
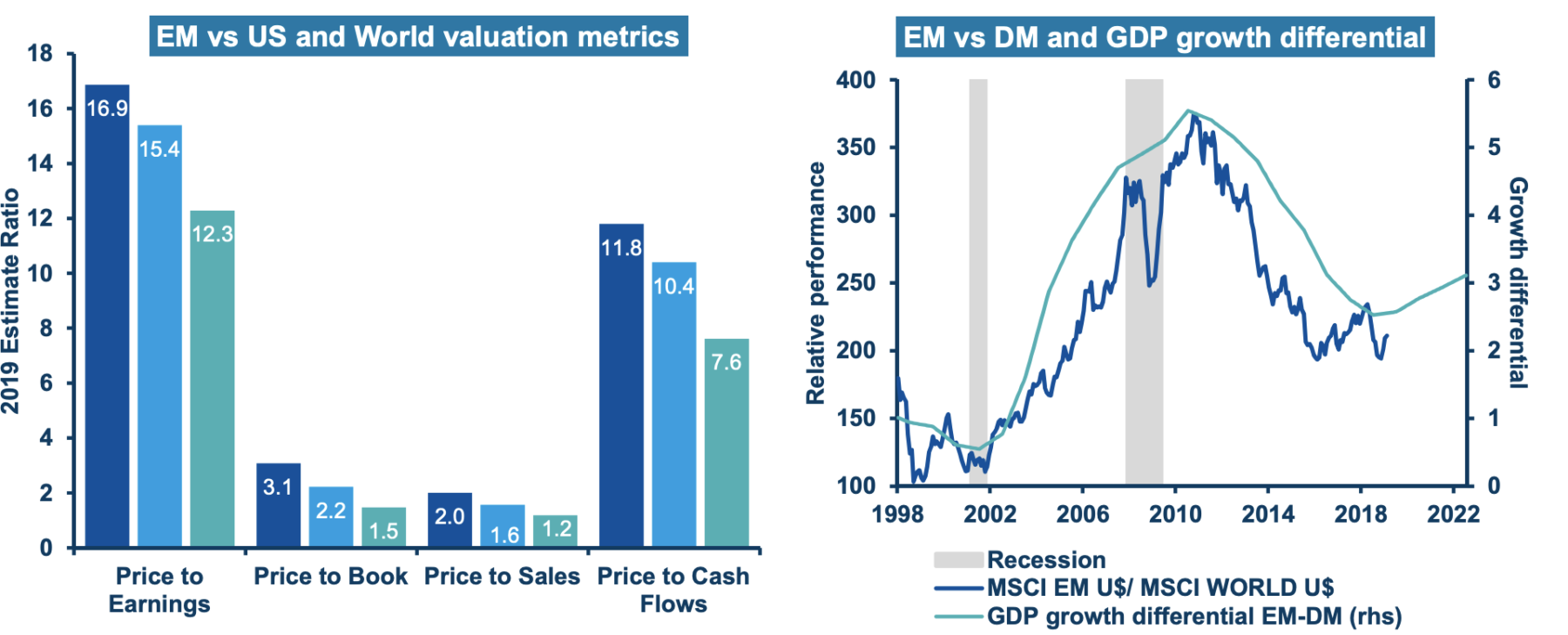 Us Market Slump Emerging Markets Post Positive Returns
Apr 24, 2025
Us Market Slump Emerging Markets Post Positive Returns
Apr 24, 2025
