Execs' Office365 Accounts Breached: Crook Makes Millions, Feds Say
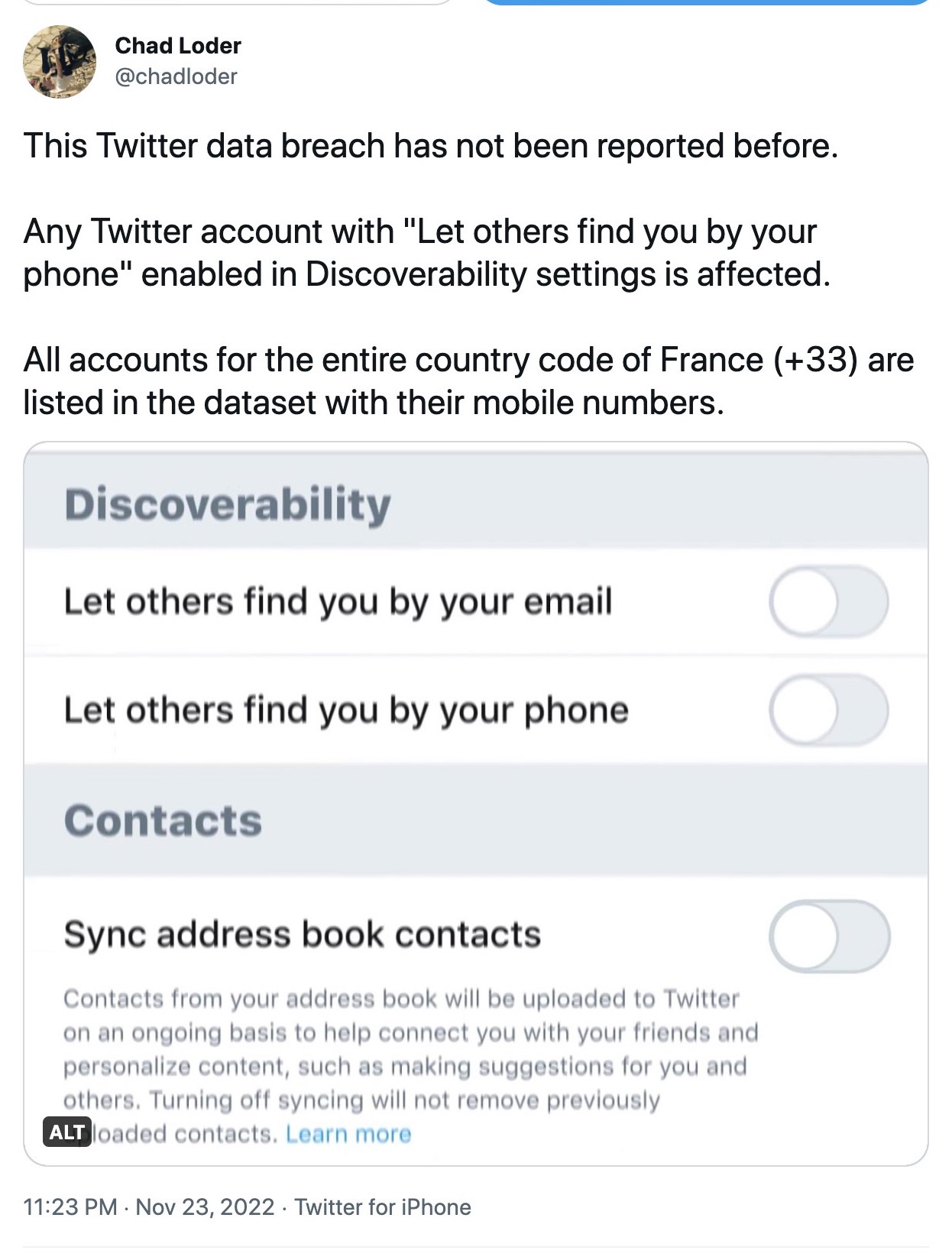
Table of Contents
The Scale and Impact of the Office365 Breach
Federal investigations reveal a sophisticated Office365 breach impacting dozens of high-profile executives across various multinational corporations. The exact number of affected executives remains undisclosed for security reasons, but sources indicate the financial losses exceed tens of millions of dollars. This large-scale breach highlights the significant financial impact of successful cyberattacks targeting even the most secure-seeming organizations. The consequences extend far beyond immediate financial losses.
- Magnitude of financial losses: Estimates suggest losses in the tens of millions of dollars, encompassing direct financial theft and the costs associated with remediation and recovery.
- Number of executives affected: While the precise number is confidential, reports indicate a significant number of executives across multiple industries and geographic locations were compromised.
- Types of data compromised: The breach involved the compromise of highly sensitive data, including financial records, confidential emails containing strategic plans, intellectual property, and personal information. This Office365 data loss had far-reaching implications.
- Geographic spread of impacted organizations: The affected companies spanned multiple countries, demonstrating the global reach of this sophisticated cybercriminal operation.
- Long-term reputational damage: Beyond financial losses, the breach has caused significant reputational damage to the involved companies, impacting investor confidence and customer trust. This reputational damage can linger for years after the initial incident.
Methods Used by the Cybercriminal
The cybercriminal employed highly sophisticated techniques to breach the executives' Office365 accounts. The investigation points to a multi-stage attack leveraging a combination of phishing scams, malware, and social engineering tactics. This wasn't a simple, opportunistic attack; it was a carefully planned and executed operation exploiting vulnerabilities within the Office365 ecosystem.
- Specific phishing techniques used: The attackers employed spear phishing, crafting highly personalized emails that appeared to originate from trusted sources. These emails contained malicious links or attachments designed to install malware on the victims' computers. Convincing email spoofing played a crucial role in gaining initial access.
- Exploitation of vulnerabilities in Office365: The attackers likely exploited known vulnerabilities in Office365 or leveraged weak passwords to gain initial access. Regular software updates and patching are crucial to mitigating these risks.
- Use of malware to gain persistent access: Once initial access was gained, malware was deployed to maintain persistent access to the accounts and exfiltrate data over extended periods. This allowed for sustained data theft and made detection more difficult.
- Potential involvement of insider threats: While not confirmed, the sophistication of the attack suggests the possibility of insider assistance, albeit unknowingly. Thorough background checks and employee awareness training are crucial in mitigating this risk.
Preventing Future Office365 Breaches: Strengthening Your Security Posture
Preventing similar Office365 breaches requires a multi-faceted approach to bolstering cybersecurity. Organizations must adopt a proactive, layered security strategy that incorporates various preventative measures. Addressing these vulnerabilities is crucial to mitigating future risks.
- Implementing multi-factor authentication (MFA): MFA adds an extra layer of security, requiring multiple forms of verification (e.g., password, one-time code) to access accounts. This significantly reduces the risk of unauthorized access, even if passwords are compromised.
- Regularly updating software and patching vulnerabilities: Regularly updating Office365 and other software applications, and promptly patching known vulnerabilities, is essential to prevent attackers from exploiting known weaknesses.
- Employing robust anti-phishing and anti-malware solutions: Implementing comprehensive anti-phishing and anti-malware solutions across all devices and networks is crucial to detect and neutralize malicious emails and software.
- Providing comprehensive cybersecurity training to employees: Educating employees about phishing techniques, malware threats, and best security practices significantly reduces the likelihood of successful phishing attacks. Regular training and awareness campaigns are vital.
- Conducting regular security audits and penetration testing: Regular security audits and penetration testing help identify vulnerabilities in your systems and processes before attackers can exploit them. This proactive approach is essential for maintaining a strong security posture.
- Utilizing advanced threat protection features within Office365: Office365 offers a range of advanced threat protection features, including advanced threat analytics and automatic malware removal. Activating and utilizing these features can significantly enhance your security.
- Implementing data loss prevention (DLP) measures: DLP measures help prevent sensitive data from leaving your organization's network without authorization. This can significantly limit the impact of a successful breach.
Conclusion
The recent Office365 breach targeting executives serves as a powerful reminder of the significant risks associated with inadequate cybersecurity. The methods used by the cybercriminal highlight the sophistication of modern cyberattacks and the potential for substantial financial and reputational damage. The scale of the financial losses and the widespread impact underscore the urgent need for organizations to strengthen their Office365 security posture. This requires a comprehensive strategy that incorporates multi-factor authentication, regular software updates, robust anti-phishing and anti-malware solutions, comprehensive employee training, regular security audits, advanced threat protection, and data loss prevention measures.
Don't become the next victim. Strengthen your Office365 security today. Learn more about best practices and advanced security solutions to protect your business from costly Office365 breaches. Invest in robust cybersecurity measures and safeguard your valuable data and reputation.

Featured Posts
-
 A Geographic Overview Of The Countrys Best New Business Locations
Apr 22, 2025
A Geographic Overview Of The Countrys Best New Business Locations
Apr 22, 2025 -
 Rapid Police Response After Fsu Security Breach Did It Quell Student Fears
Apr 22, 2025
Rapid Police Response After Fsu Security Breach Did It Quell Student Fears
Apr 22, 2025 -
 Us Protests Against Trump Voices From Across The Nation
Apr 22, 2025
Us Protests Against Trump Voices From Across The Nation
Apr 22, 2025 -
 Karen Reads Legal Battles A Year By Year Account
Apr 22, 2025
Karen Reads Legal Battles A Year By Year Account
Apr 22, 2025 -
 Land Your Dream Private Credit Job 5 Dos And Don Ts To Follow
Apr 22, 2025
Land Your Dream Private Credit Job 5 Dos And Don Ts To Follow
Apr 22, 2025
