Executive Office365 Inboxes Targeted In Multi-Million Dollar Cybertheft
Table of Contents
The Growing Threat of Office365 Compromises
Office365 security breaches, particularly those targeting executive-level accounts, are on the rise. Cybercriminals are employing increasingly sophisticated techniques to gain unauthorized access and exploit vulnerabilities. This trend is driven by several factors:
- Increased sophistication of phishing and malware attacks: Phishing emails are becoming harder to distinguish from legitimate communications, often incorporating personalized details to increase their effectiveness. Malware is also evolving, becoming more adept at evading detection and accessing sensitive information.
- Exploitation of vulnerabilities in poorly configured Office365 environments: Many organizations fail to implement essential security measures, leaving their Office365 environments vulnerable to attack. Weak passwords, a lack of multi-factor authentication, and outdated software all contribute to this vulnerability.
- The use of advanced persistent threats (APTs): APTs are sophisticated, long-term attacks designed to maintain covert access to a system over an extended period. These attacks are difficult to detect and often result in significant data breaches.
- Rise in Business Email Compromise (BEC) scams: BEC scams involve criminals impersonating executives or other trusted individuals to trick employees into transferring funds or revealing sensitive information. These scams often result in substantial financial losses.
The evolution of these attacks is alarming. Recent reports show a significant increase in the average cost of a data breach, highlighting the escalating financial stakes involved in securing executive Office365 accounts. The stakes are high; a successful breach can lead to irreparable reputational damage and significant financial losses.
Methods Employed in Executive Office365 Cybertheft
Cybercriminals utilize a range of sophisticated methods to compromise Executive Office365 inboxes. These methods often combine technical expertise with social engineering tactics:
- Spear phishing: This highly targeted form of phishing focuses on specific individuals, often executives, using personalized information to increase the likelihood of success. These emails can appear incredibly convincing, making them difficult to identify as malicious.
- Malware: Malicious software, such as ransomware and spyware, is used to gain unauthorized access to systems, steal data, and disrupt operations. Once inside, malware can be used to exfiltrate sensitive information, including financial records and intellectual property.
- Credential stuffing: This technique involves using stolen usernames and passwords obtained from other data breaches to attempt access to Office365 accounts. This is often automated using bots, making it a highly efficient method for cybercriminals.
- Social engineering: This involves manipulating individuals into revealing sensitive information, such as passwords or access codes, through deception or manipulation. This can be done through phone calls, emails, or even in-person interactions.
The sophistication of these methods underscores the need for robust security measures. Understanding the techniques used is critical in developing effective defenses. For instance, a successful spear phishing attack against a CEO can result in millions of dollars being fraudulently transferred.
The Devastating Consequences of a Successful Breach
The consequences of a successful Executive Office365 breach can be devastating, impacting multiple aspects of an organization:
- Significant financial losses: Fraudulent wire transfers, data extortion, and the costs associated with recovery efforts can result in substantial financial losses. The financial impact can cripple even large organizations.
- Reputational damage: A data breach can severely damage an organization's reputation, leading to a loss of customer trust and potential business disruptions. This reputational damage can be long-lasting and difficult to recover from.
- Legal ramifications: Organizations may face legal liabilities and regulatory penalties under laws like GDPR and CCPA, resulting in significant fines and legal fees. Non-compliance can lead to further reputational damage and financial penalties.
- Cost of incident response, remediation, and recovery: The process of investigating a breach, containing the damage, and restoring systems can be incredibly expensive, involving forensic experts, legal counsel, and IT specialists.
The cumulative effect of these consequences can be catastrophic. Real-world examples demonstrate that the long-term impact of a major breach can far exceed the immediate financial losses.
Protecting Your Executive Office365 Inboxes: Proactive Security Measures
Protecting your organization from these sophisticated attacks requires a multi-layered approach focusing on proactive security measures:
- Multi-factor authentication (MFA): Implementing MFA for all accounts adds an extra layer of security, significantly reducing the risk of unauthorized access, even if passwords are compromised.
- Security awareness training: Regular training for all employees, especially executives, is crucial to educate them about phishing techniques, social engineering tactics, and safe online practices. Simulations and phishing tests can significantly increase awareness.
- Advanced threat protection solutions: Utilizing solutions like Microsoft Defender for Office 365 offers advanced protection against malware, phishing attacks, and other threats, providing real-time threat detection and response.
- Strong password policies: Enforce strong, unique passwords for all accounts and encourage regular password changes. Password managers can assist with this.
- Regular security audits and penetration testing: Conducting regular security audits and penetration testing helps identify vulnerabilities in your systems and processes, allowing you to address them before they can be exploited.
By implementing these measures, organizations can significantly reduce their risk of becoming victims of Executive Office365 cybertheft. A proactive approach is far more cost-effective than reactive measures taken after a breach.
Conclusion
The targeting of Executive Office365 inboxes for multi-million dollar cyberthefts is a growing and increasingly sophisticated threat. The consequences of a successful breach can be financially crippling, severely damaging to reputation, and fraught with legal ramifications. Protecting your organization requires a proactive approach, combining robust security measures with comprehensive employee training. Don't wait until it's too late – implement multi-factor authentication, advanced threat protection, and thorough security awareness training to safeguard your Executive Office365 inboxes and prevent costly cybertheft. Secure your Office365 environment today and protect your business from this escalating threat.
Featured Posts
-
 John Travoltas Low Rotten Tomatoes Score A Critical Analysis
Apr 24, 2025
John Travoltas Low Rotten Tomatoes Score A Critical Analysis
Apr 24, 2025 -
 Canadian Dollars Mixed Performance Gains Against Us Dollar Losses Against Others
Apr 24, 2025
Canadian Dollars Mixed Performance Gains Against Us Dollar Losses Against Others
Apr 24, 2025 -
 Blue Origins Rocket Launch Abruptly Halted By Subsystem Failure
Apr 24, 2025
Blue Origins Rocket Launch Abruptly Halted By Subsystem Failure
Apr 24, 2025 -
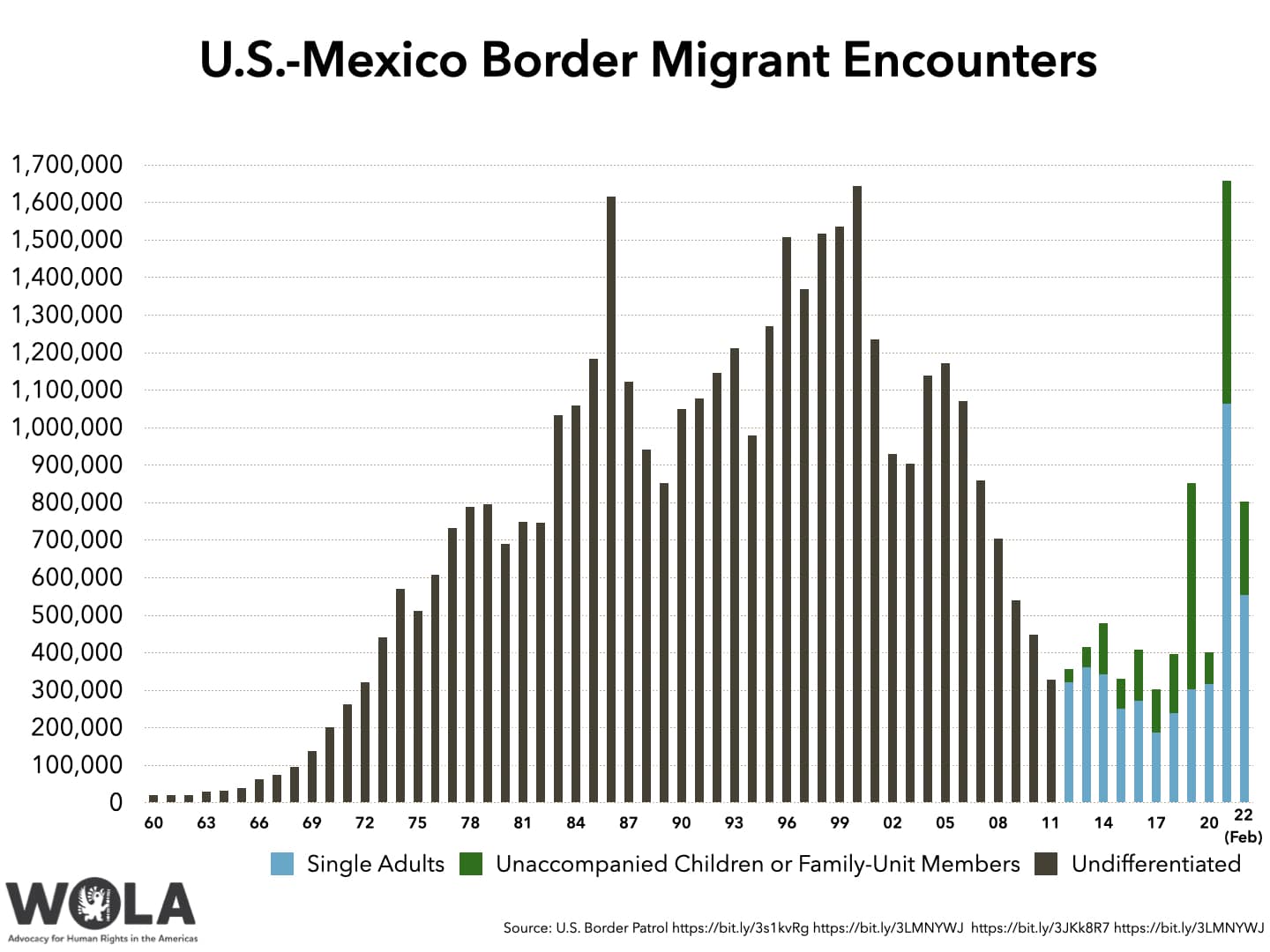 Fewer Border Crossings White House Reports Decline In Canada U S Border Apprehensions
Apr 24, 2025
Fewer Border Crossings White House Reports Decline In Canada U S Border Apprehensions
Apr 24, 2025 -
 Trump Affirms Powells Continued Role As Fed Chair
Apr 24, 2025
Trump Affirms Powells Continued Role As Fed Chair
Apr 24, 2025
