Hegseth's Signal Chat: Leaked Military Plans With Family
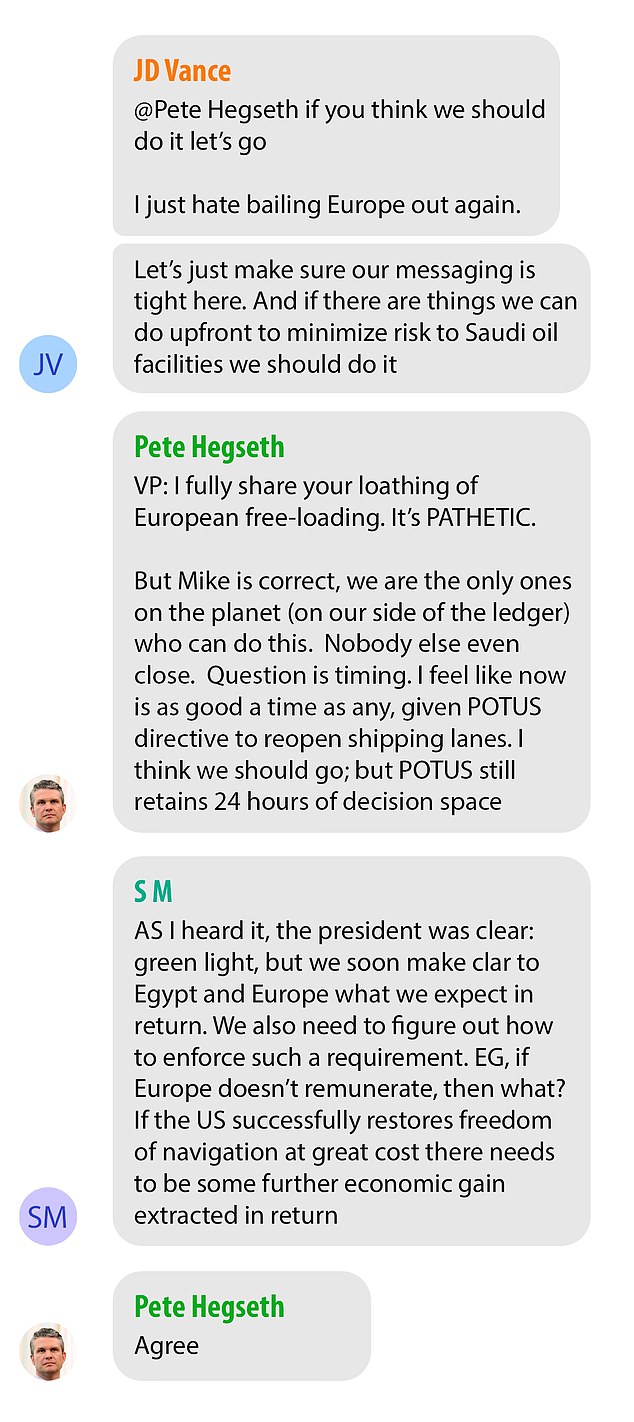
Table of Contents
The Leaked Information: What Military Plans Were Compromised?
The exact nature of the leaked military plans remains partially undisclosed to protect national security. However, reports suggest the information involved highly sensitive data potentially jeopardizing ongoing operations and future strategic planning. The gravity of the situation stems from the potential impact on both military personnel and national security interests. The potential breach represents a serious threat to operational security.
- Deployment Schedules: Leaked schedules could compromise troop positioning and leave units vulnerable to attack.
- Troop Movements: Disclosing troop movements could allow adversaries to anticipate military actions and plan countermeasures.
- Equipment Specifications: Revealing details about military equipment could provide adversaries with crucial intelligence to develop countermeasures.
- Operational Strategies: The disclosure of operational strategies could significantly undermine military effectiveness and lead to mission failures.
The severity of the potential compromise underscores the critical need for stringent security protocols within the military and heightened awareness of communication security practices among all personnel.
Hegseth's Response and the Ongoing Investigation
At the time of writing, Pete Hegseth's public response to the alleged leak is [Insert details of Hegseth's response here, if available. If not, state that his response is unavailable or under investigation and emphasize the ongoing nature of the investigation]. Official investigations are underway, focusing on determining the extent of the data breach, how the leak occurred, and who is responsible. Potential legal ramifications and disciplinary actions remain a possibility depending on the findings of the investigation.
- Hegseth's Statement: [Summarize key points of his response, if any, or state the lack of public statement.]
- Investigation Timeline: [Provide a timeline of the investigation, if available, or state the ongoing nature of the investigation]
- Potential Charges: [List potential legal charges, if any are known, or state that potential charges are currently under consideration.]
- Disciplinary Actions: [Discuss potential disciplinary actions, if any are known, or state that potential disciplinary actions are currently under consideration]
Signal App Security and Privacy Concerns
Signal, known for its end-to-end encryption, is often touted as a secure messaging platform. However, this incident raises questions about its overall security and the potential for vulnerabilities, especially in the context of high-stakes communication involving classified information. While end-to-end encryption protects messages from being intercepted by third parties, it does not guarantee complete security against breaches resulting from compromised devices or user error.
- Signal's Security Pros: End-to-end encryption, open-source code allowing for independent security audits.
- Signal's Security Cons: Reliance on user security practices; vulnerability to phishing attacks and malware.
- Potential Exploits: [Discuss possible ways the leak might have occurred, e.g., compromised devices, phishing, social engineering.]
- Alternatives: Explore alternative secure communication platforms suitable for handling sensitive information within the military context.
The Broader Implications for National Security and Communication Protocols
This incident highlights significant vulnerabilities in military communication security and the critical need for enhanced protocols. The alleged leak could damage trust and morale within the ranks, and significantly impact operational effectiveness. The incident necessitates a comprehensive review of existing communication protocols, potentially leading to policy changes and stricter security measures.
- Policy Changes: Expect reviews and potential changes to regulations concerning the handling of sensitive information and the use of messaging apps.
- Increased Security Measures: Likely implementation of more stringent security measures, including stricter device security protocols and enhanced training.
- New Protocols: The development and implementation of new communication protocols, potentially including more secure platforms or stricter guidelines.
- Training Initiatives: Increased training for military personnel on secure communication practices and the risks of using unsecured channels.
Conclusion: Understanding the Ramifications of Hegseth's Signal Chat and Future Implications
The Hegseth Signal chat controversy underscores the severe risks associated with leaking sensitive military information, regardless of the platform used. The potential consequences of such breaches on national security and military operations cannot be overstated. Secure communication protocols are paramount, and this incident serves as a stark reminder of the need for continuous vigilance and improvement in data protection strategies within the military and government. What are your thoughts on the Hegseth Signal chat incident and its impact on national security? Share your insights in the comments below!

Featured Posts
-
 Trumps Economic Agenda Who Pays The Price
Apr 22, 2025
Trumps Economic Agenda Who Pays The Price
Apr 22, 2025 -
 Ohio Train Derailment Toxic Chemical Lingering In Buildings
Apr 22, 2025
Ohio Train Derailment Toxic Chemical Lingering In Buildings
Apr 22, 2025 -
 U S China Relations Breakdown And The Looming Cold War
Apr 22, 2025
U S China Relations Breakdown And The Looming Cold War
Apr 22, 2025 -
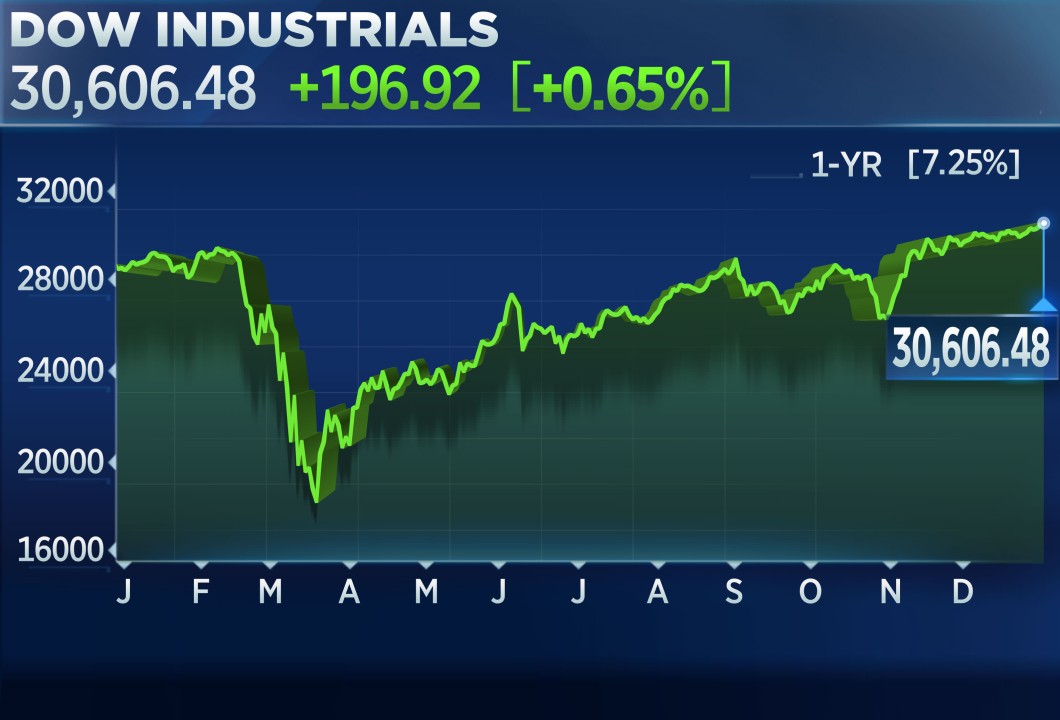 Trade War Impact Todays Stock Market Analysis And Dow Futures
Apr 22, 2025
Trade War Impact Todays Stock Market Analysis And Dow Futures
Apr 22, 2025 -
 Are Higher Stock Prices Sustainable Investors Face Difficult Choices
Apr 22, 2025
Are Higher Stock Prices Sustainable Investors Face Difficult Choices
Apr 22, 2025
